Directory Traversal and Source code disclosure vulnerability
(What's the main issue in the application?)
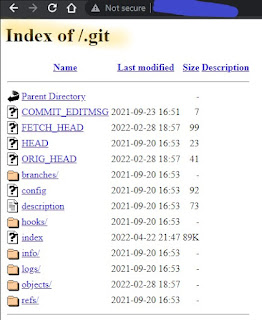
The web server exposes a Source Code via version control system - Git.
The Directory Listing feature that was enabled on the server side is discloses the directories that stores sensitive files that are related to the Source Code
(Who can access? What are the possible risks)
An external attacker may download the source code and disclose sensitive information regarding the development and possibly other sensitive data.
In the application I found two ways of disclosing source code.
Instance#1:
After performing nikto I found directories as shown
An attacker may use automated tools to discover, download and extract git repositories. https://github.com/internetwache/GitTools
Note: Due to the fact that the server has Directory Listing feature enabled, makes even easier to download the git repositories using simple wget command. wget --mirror -I .git TARGET.COM/.git/
Instance#2:
The attacker may run Directory Fuzzing attack and disclose directories that stores sensitive files.
/backend
/test
/frontend





Comments
Post a Comment